Terminating SSL Requests
The following sections describe how to terminate requests using SSL before or within Oracle HTTP Server, where the mod_wl_ohs module forwards requests to WebLogic Server. Whether you terminate SSL before the request reaches Oracle HTTP Server or when the request is in the server, depends on your topology. A common reason to terminate SSL is for performance considerations when an internal network is otherwise protected with no risk of a third-party intercepting data within the communication. Another reason is when WebLogic Server is not configured to accept HTTPS requests.
This section includes the following topics:
About Terminating SSL at the Load Balancer
If you are using another device such as a load balancer or a reverse proxy which terminates requests using SSL before reaching Oracle HTTP Server, then you must configure the server to treat the requests as if they were received through HTTPS. The server must also be configured to send HTTPS responses back to the client.
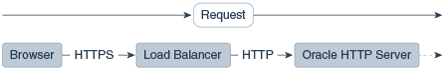
Figure 9-1 illustrates an example where the request transmitted from the browser through HTTPS to WebLogic Server. The load balancer terminates SSL and transmits the request as HTTP. Oracle HTTP Server must be configured to treat the request as if it was received through HTTPS.
Terminating SSL at the Load Balancer
To instruct the Oracle HTTP Server to treat requests as if they were received through HTTPS, configure the httpd.conf file with the SimulateHttps directive in the mod_certheaders module.
For more information on mod_certheaders module, see mod_certheaders Module—Enables Reverse Proxies.
Note:
This procedure is not necessary if SSL is configured on Oracle HTTP Server (that is, if you are directly accessing Oracle HTTP Server using HTTPS).
- Configure the
httpd.conf configuration file with the external name of the server and its port number, for example:ServerName <www.company.com:port>
- Configure the
httpd.conf configuration file to load the mod_certheaders module, for example: - Configure the
SimulateHttps directive at the bottom of the httpd.conf file to send HTTPS responses back to the client, for example:# For use with other load balancers and front-end devices:
SimulateHttps On
- Restart Oracle HTTP Server and test access to the server. Especially, test whether you can access static pages such as
https://host:port/index.htmlTest your configuration as a basic setup. If you are having issues, then you should troubleshoot from here to avoid overlapping with other potential issues, such as with virtual hosting.
- Ideally, you may want to configure a
VirtualHost in the httpd.conf file to handle all HTTPS requests. This separates the HTTPS requests from the HTTP requests as a more scalable approach. This may be more desirable in a multi-purpose site or if a load balancer or other device is in front of Oracle HTTP Server which is also handling both HTTP and HTTPS requests.The following sample instructions load the mod_certheaders module, then creates a virtual host to handle only HTTPS requests.
# Load correct module here or where other LoadModule lines exist:
LoadModule certheaders_module libexec/mod_certheaders.so
# This only handles https requests:
<VirtualHost <name>:<port>
# Use name and port used in url:
ServerName <www.company.com:port>
SimulateHttps On
# The rest of your desired configuration for this VirtualHost goes here
</VirtualHost>
- Restart Oracle HTTP Server and test access to the server, First test a static page such as
https://host:port/index.html and then your test your application.
About Terminating SSL at Oracle HTTP Server
If SSL is configured in Oracle HTTP Server but not on Oracle WebLogic Server, then you can terminate SSL for requests sent by Oracle HTTP Server.
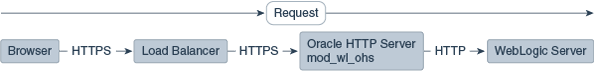
The following figures illustrate request flows, showing where HTTPS stops. In Figure 9-2, an HTTPS request is sent from the browser. The load balancer transmits the HTTPS request to Oracle HTTP Server. SSL is terminated in Oracle HTTP Server and the HTTP request is sent to WebLogic Server.
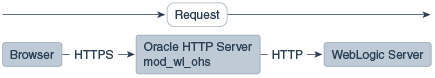
In Figure 9-3 there is no load balancer and the HTTPS request is sent directly to Oracle HTTP Server. Again, SSL is terminated in Oracle HTTP Server and the HTTP request is sent to WebLogic Server.
Terminating SSL at Oracle HTTP Server
To instruct the Oracle HTTP Server to treat requests as if they were received through HTTPS, configure the WLSProxySSL directive in the mod_wl_ohs.conf file and ensure that the SecureProxy directive is not configured.
- Configure the
mod_wl_ohs.conf file to add the WLSProxySSL directive for the location of your non-SSL configured managed servers.For example:
WLProxySSL ON
- If using a load balancer or other device in front of Oracle HTTP Server (which is also using SSL), you might need to configure the
WLProxySSLPassThrough directive instead, depending on if it already sets WL-Proxy-SSL. - Ensure that the
SecureProxy directive is not configured, as it will interfere with the intended communication between the components.This directive is to be used only when SSL is used throughout. The
SecureProxy directive is commented out in the following example:
# To configure SSL throughout (all the way to WLS):
# SecureProxy ON
# WLSSLWallet "<Path to Wallet>"
- Enable the WebLogic Plug-In flag for your managed servers or cluster.
By default, this option is not enabled. Complete the following steps to enable the WebLogic Plug-In flag:
- Log in to the Oracle WebLogic Server Administration Console.
- In the Domain Structure pane, expand the Environment node.
- Click on Clusters.
- Select the cluster to which you want to proxy requests from Oracle HTTP Server.
The Configuration: General tab appears.
- Scroll down to the Advanced section, expand it.
- Click Lock and Edit.
- Set the WebLogic Plug-In Enabled to yes.
- Click Save and Activate the Changes.
- Restart the servers for the changes to be effective.
- Restart Oracle HTTP Server and test access to a Java application.
For example: https://host:port/path/application_name.



No comments:
Post a Comment